Introduction
If the antivirus blocks sites by mistake, it should not be a mistake. The fact is that in communication or with classmates, where it wants to enter, in reality, they may turn out to be fake (1). They have almost the same address (one letter changed) and the same content, but they are created by fraudsters to steal passwords (2). These sites in communication and classmates (and not only) are almost indistinguishable from the real thing. Nodes, avast, and AVG know about them-so they block them to protect it from stealing passwords or viruses (3, 4). If it fully trusts the reliability of the blocked sites, it can fix this without disabling the antivirus (5). It can do the same with other antiviruses that block malicious sites. Everyone employs these techniques (6). It can add files (programs) to exclusions in the same way, so that the antivirus does not block them, only the settings are slightly different (it needs to select other options) (7). Of course, it is antivirus, but it is better not to do it. Never send SMS (8).
It can dial a phone number, which sometimes it needs, but it can’t send SMS in any case. A phone number is entered so it can retrieve the password (9). Such activities include classmates, emails, Skype, bank sites and more (10). There is nothing wrong with this; on the contrary, it is even better because no one can change its password without its knowledge (11). If in doubt, they warn, though the developers take great care to ensure that their antiviruses do not block trusted sites and programs (12). They have their own reasons (they protect their interests), then manually add sites and files to the exceptions, using the method described earlier, or disable them for a while, although disabling does not always help (13, 14).
When it changes its antivirus program, it often happens that it faces the problem of complete inability to visit previously accessible sites (15). Why is this happening? Is antivirus really a virus? Of course not, because here everything is very simple: the antivirus program blocks websites because it cares about the security of its computer! Yes, this problem is solved very simply: in the exceptions it needs to include sites that it has visited before (now the antivirus program does not allow it) (16).
Literature review
Before looking for methods to solve problems with network and router settings, check the status of its account with the provider and the reliability of the network cable. This solves the problem in half of the cases (1). Sometimes, Internet access may be blocked by the computer’s own security agents, such as a firewall or antivirus. Define the obstacle. Windows Firewall 8 is very easy-turn it off in the system settings and check the connection. If the network appears, then the problem is detected (2).
If the block comes from an antivirus, it needs to disable the program directly or complete the relevant processes through the task manager. The main function of a firewall is to check data coming from the Internet and block it from causing concern (11). There are two modes of listing: “white” and “black.” White-blocks everything except allowed and black-allows everything except forbidden. Even after that, the full customization firewall needs to set permissions for new applications. There is a special list of programs that are allowed to exchange data with the Internet, and if what it needs is blocked, then it needs to configure permissions for it in this list (17). In addition, it can set notifications so that if a new application is blocked, it has the option to leave everything as it is and allow access to this program. For example, it can block Internet access to Skype or Google Chrome, or vice versa, leave access only to certain work programs (18).
If it has problems connecting via Wi-Fi, it needs to determine the source of the problem. It can be a laptop, router, or provider. If all devices are connected to the router and work normally with the Internet, the reason is in the laptop. If vice versa, the network cable is connected to the computer and the Internet works, it needs to do the router settings (19). If all else fails, contact its provider ’s technical support. If the problem is with the laptop but all the above settings are in order, run system diagnostics for viruses and device activity (20).
Proposed model
The proposed application works several times faster than its competitors. At the same time, even paid antiviruses can be jealous of ensuring security. Encrypted and polymorphic viruses can be detected using deep emulation technology. The use of other technologies used by third- party programs may not provide useful results. Attackers sometimes hide viruses in archives. Most free programs cannot scan rar or zip archives. The proposed antivirus copes well with this task. In 99% of cases, the threat will be detected. When a user accesses any type of file, the antivirus starts scanning it. The same happens with the operating system accessing the files. Thus, system protection is carried out continuously, in real time. If a dangerous file is detected, it will be blocked. An intuitive clear interface allows even an inexperienced user to cope with antivirus management. The program allows it to add any applications to the exceptions. Selection of the optimal interface includes the following, as shown in Figure 1.
A function that starts an antivirus function on behalf of another user (this is useful for system administrators and allows them to integrate the entire complex into another infrastructure). Antivirus was created to protect against various types of threats and computer data waiting for users on the Internet or when using unverified programs. It can protect against the following misfortunes shown in Figure 2.
● Viruses
● Trojans
● Worms
● Cryptographic malware
● Polymorph malware
It can find its laptop’s MAC address by typing IP configuration/all in the command prompt. Also, the router has speed limit settings for each client, so it can allow the speed to be maximum or limit it to two kilobits per second. The proposed model provides real-time quality protection. This can greatly improve the accuracy of archive tests and uncompiled files. An advanced analysis system allows it to detect all types of malicious files that have not yet been included in the virus database. The latter is updated at least once a day. This is shown in Figure 2.
Therefore, there is no need to constantly remove a useful application from quarantine that is considered antivirus malware. A specially developed mode for optimizing its system resources will allow it to ensure comfortable work even when the antivirus is running. Access to the most common tasks is more conveniently organized. It can fully scan its computer or removable media in a limited number of steps with the Express Scan feature. In this mode, the system scans the most dangerous areas. Updating the app is very quick and easy. It is activated by a table and pressing a few interface buttons. The full automation of the program is very efficient and helps detect and remove any threat as soon as possible.
Results and discussions
The proposed intelligent deep learning (IDL) was compared with the existing Optimal control strategy (OCS), Malware Detection Using Machine Learning Algorithms (MDMLA), and Adoption, Assessment of Machine Learning Algorithms (AAMLA), and distributed scheduling and QoS localized routing (DSQLR).
Internet speed management
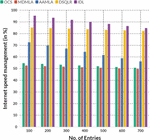
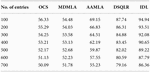
Problems with Internet speed can be a signal for help from the router-maybe it hasn’t removed the factory image from it, it’s covered by something, or it’s overheating for other reasons. As shown in Figure 3, if it does not provide the device with normal ventilation, it will not last long and will be very inefficient. The comparison of Internet speed management is discussed in Table 1.
Router management
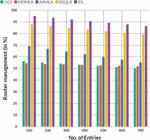
If it suspects a problem with the router, it should connect the network cable to its laptop or computer to check. If the Internet does not work automatically, create a new cable connection and enter the login and password provided by the provider. It may need to enter additional settings. The comparison of router management was discussed in Table 2.
Figure 4 demonstrates the comparison of internet speed management. Protocols in adapter properties set up a connection through a router occur through the device’s web interface. The router sometimes comes with a setup disk, but it can do without it. For the initial setup, it is best to connect the router directly to the laptop, then via an internet cable. Connecting to the mains is done last.
Antivirus management
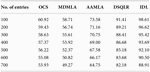
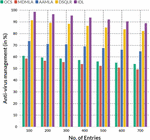
First, immediately after installing and running the program, the antivirus blocks sites it considers dangerous. Naturally, not all sites are classified, but a real antivirus program means that a reinsurer operates according to the rule that it’s better to walk around than step on the rack. The comparison of antivirus management was discussed in Table 3.
Figure 5 shows the comparison of antivirus management. The sad thing is that the MBR virus cannot be deleted because it is written on the first line. Boot sector settings. In short, the only way is a complete reinstallation setting, naturally with a complete loss of all data.
Conclusion
If it does not have enough time to wait for a specialist, does not want to spend money, and feels like a confident personal computer (PC) user, then it can try to set up the Internet connection itself, using various instructions and recommendations. It will take two to three times more time and energy than going to the master, but it will give useful experience in the future. In this age of new technologies, an antivirus for a computer can be compared to a virus vaccine for a person. If its antivirus is not working properly, the PC will not last long. But after installing the antivirus, it will not be able to access the Internet. This condition often occurs in the workplace. A router, with incorrect settings, can distribute Wi-Fi without access to the network. Read on to learn how to properly set up its router. One of the reasons for connecting without a network is to protect the Wi-Fi network from unauthorized access by blocking it by MAC address. It can find out how to fix this problem on the router manufacturer ’s website, or it can find the list of allowed or blocked addresses in the settings itself and add/remove the address of its laptop.
Author contributions
All authors listed have made a substantial, direct, and intellectual contribution to the work, and approved it for publication.
References
1. Raja S, Logeshwaran J, Venkatasubramanian S, Jayalakshmi M, Rajeswari N, Olaiya NG, et al. OCHSA: designing energy-efficient lifetime-aware leisure degree adaptive routing protocol with optimal cluster head selection for 5G communication network disaster management. Sci Programming. (2022). doi: 10.1155/2022/5424356
2. Dasiffi D, Viaeetia’ M, Ilia N, Stankovia M, Beko M. Application of deep learning algorithms and architectures in the new generation of mobile networks. Serbian J Electr Eng. (2021) 18:397–426. doi: 10.2298/SJEE2103397D
3. Gopi B, Logeshwaran J, Gowri J, Kiruthiga T. The moment probability and impacts monitoring for electron cloud behavior of electronic computers by using quantum deep learning model. NeuroQuantology. (2022) 20:6088–6100.
4. Li Y, Qiu L, Zhang Y, Mahajan R, Rozner E. Predictable performance optimization for wireless networks. ACM SIGCOMM Comput Commun Rev. (2008) 38:413–426. doi: 10.1145/1402946.1403005
5. Logeshwaran J, Malik JA, Adhikari N, Joshi SS, Bishnoi P. IoT-TPMS: an innovation development of triangular patient monitoring system using medical internet of things. Int J Health Sci. (2022) 6:9070–9084. doi: 10.53730/ijhs.v6nS5.10765
6. Lin X, Shroff NB, Srikant R. A tutorial on cross-layer optimization in wireless networks. IEEE J Sel Areas Commun. (2006) 24:1452–1463. doi: 10.1109/JSAC.2006.879351
7. Ramesh G, Logeshwaran J, Aravindarajan V, Thachil F. Eliminate the interference in 5g ultra-wide band communication antennas in cloud computing networks. ICTACT J Microelectron. (2022) 8:1338–1344.
8. Wu Q, Zhang R. Beamforming optimization for wireless network aided by intelligent reflecting surface with discrete phase shifts. IEEE Trans Commun. (2019) 68:1838–1851. doi: 10.1109/TCOMM.2019.2958916
9. Yeshwanth MV, Kalluri R, Rao MS, Kumar RK, Bind- Humadhava BS. Adoption and assessment of machine learning algorithms in security operations centre for critical infrastructure. In: Pillai RK, Ghatikar G, Sonavane VL, Singh BP editors. ISUW 2020. Lecture notes in electrical engineering. (Vol. 847), Singapore: Springer (2022). p. 395–407. doi: 10.1007/978-981-16-9008-2_38
10. Logeshwaran J, Karthick S. A smart design of a multi-dimensional antenna to enhance the maximum signal clutch to the al lowable standards in 5G communication networks. ICTACT J Microelectron. (2022) 8:1269–74.
11. Johansson M, Xiao L. Cross-layer optimization of wireless networks using nonlinear column generation. IEEE Trans Wireless Commun. (2006) 5:435–445. doi: 10.1109/TWC.2006.1611067
12. Jasmine J, Yuvaraj N, Logeshwaran J. DSQLR-A distributed scheduling and QoS localized routing scheme for wireless sensor network. Recent Trends Inf Technol Commun Ind 4.1. (2022) 1:47–60.
13. Wang F, Lu Y, Li Q, Wang C, Bai Y. A co- evolutionary algorithm-based malware adversarial sample generation method. Proceedings of the IEEE conference on dependable and secure computing (DSC). Piscataway, NJ: IEEE (2022). p. 1–8. doi: 10.1109/DSC54232.2022.9888884
14. Ramkumar M, Logeshwaran J, Husna T. CEA: certification based encryption algorithm for enhanced data protection in social networks. Fundamentals Appl Math Soft Comput. (2022) 1:161–170.
15. Choudhary S, Sharma A. Comparison study of machine learning algorithm and data science based machine learning algorithm malware detection. Math Stat Eng Appl. (2022) 71:01–07. doi: 10.17762/msea.v71i3s.2
16. Logeshwaran J. Thecontrol and communicationman- agement for ultra dense cloud system using fast Fourier algorithm. ICTACT J Data Sci Mach Learn. (2022) 3:281–284.
17. Verma NK, Singh V. A rational approach to improve access time of apriori algorithm by applying inner join in a arm to redefining Fis in textual data. ECS Trans. (2022) 107:7749. doi: 10.1149/10701.7749ecst
18. Saravanakumar K, Logeshwaran J. Auto-Theft prevention system for underwater sensor using lab view. Int J Innov Res Comput Commun Eng. (2016) 4:1750–1755.
19. Tian Z, Gao Z. Multi-carrier steganography algorithm based on executable program. In: Sun X, Zhang X, Xia Z, Bertino E editors. Proceedings of the international conference on artificial intelligence and security. Cham: Springer (2022). p. 363–372. doi: 10.1007/978-3-031-06791-4_29